This article will discuss the importance of DLP solutions, how they work, and key strategies for preventing data leaks.Understand the key strategies to prevent data leakage, prevent and control data leakage, and protect personal information security.
Understanding Data Leak Prevention
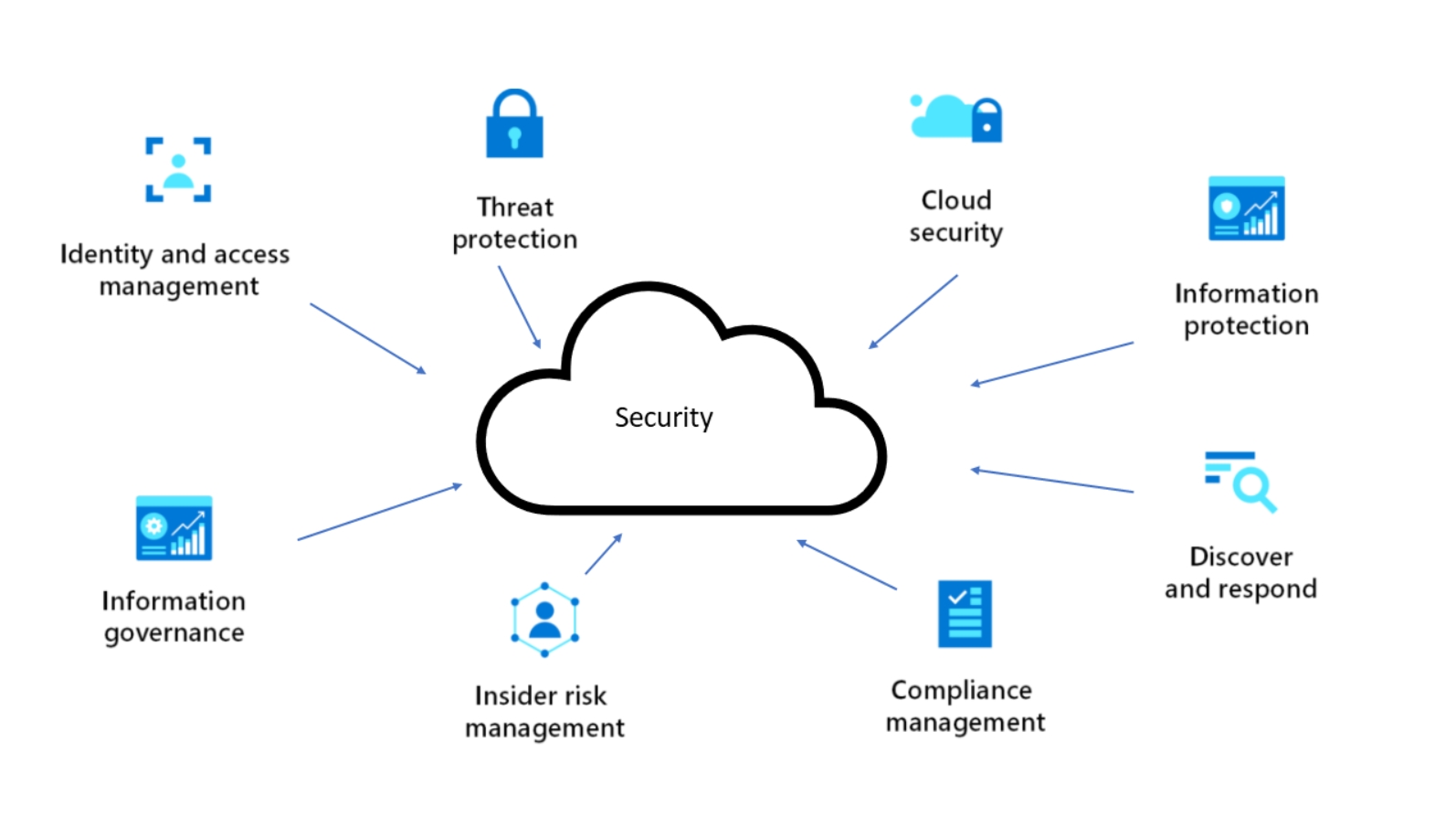
Data leak prevention refers to the strategies and technologies used to detect, monitor, and protect sensitive data from unauthorized access and transmission. DLP solutions are designed to ensure that confidential information, such as financial records, personal data, intellectual property, and other sensitive content, remains secure within an organization’s boundaries and is not inadvertently or maliciously shared outside. The primary goal of DLP is to prevent data breaches and ensure compliance with regulatory standards.
How Data Leak Prevention Solutions Work
DLP solutions operate through a combination of policies, rules, and technologies to safeguard data. Here’s a closer look at the core components:
Data Identification and Classification: The first step in DLP is identifying and classifying sensitive data. This involves scanning data at rest (stored data), in motion (data being transmitted), and in use (data being accessed or processed). Classification labels, such as confidential, internal use, or public, help determine the appropriate level of protection required.
Policy Definition and Enforcement: Based on the classification, organizations establish policies that dictate how data should be handled. These policies define which data can be shared, who can access it, and under what circumstances. DLP solutions enforce these policies by monitoring data activity and blocking or flagging any actions that violate the rules.
Data Monitoring and Analysis: Continuous monitoring of data activity is crucial for detecting potential leaks. DLP solutions track data usage patterns, access attempts, and transfer activities in real-time. Advanced analytics and machine learning algorithms can identify anomalies and potential threats, such as unusual data transfers or access from unauthorized locations.
Incident Response and Reporting: When a potential data leak is detected, the DLP solution triggers an incident response protocol. This may include alerting security teams, blocking data transfers, or quarantining suspicious files. Detailed reporting and audit trails provide insights into the incident, helping organizations understand the root cause and take corrective actions to prevent future occurrences.
User Education and Training: An often-overlooked aspect of DLP is educating users about data security best practices. Regular training sessions and awareness programs can help employees recognize potential risks, understand the importance of data protection, and adhere to organizational policies. A well-informed workforce is a critical line of defense against data leaks.
Key Strategies for Data Leak Prevention
To implement an effective DLP solution, organizations should consider the following strategies:
Comprehensive Data Inventory: Maintain an up-to-date inventory of all sensitive data, including its location, format, and access permissions. This enables accurate classification and policy enforcement.
Granular Access Controls: Implement role-based access controls (RBAC) to ensure that employees only have access to the data necessary for their job functions. Regularly review and adjust access permissions as needed.
Encryption and Data Masking: Use encryption to protect data both at rest and in transit. Data masking techniques can also be employed to obscure sensitive information, making it less accessible to unauthorized users.
Regular Audits and Compliance Checks: Conduct regular audits to ensure compliance with data protection regulations and internal policies. Use these audits to identify and address potential vulnerabilities.
Incident Response Planning: Develop and test an incident response plan to quickly and effectively address data leaks. This plan should include clear roles and responsibilities, communication protocols, and recovery procedures.
Conclusion
Data leak prevention is critical for protecting sensitive information and maintaining organizational integrity. Proactive strategies, such as comprehensive data inventories, granular access controls, encryption, regular audits, and effective incident response planning, further enhance data security. Investing in a comprehensive DLP solution ensures that sensitive data remains protected, fostering trust and compliance in an increasingly digital world.





